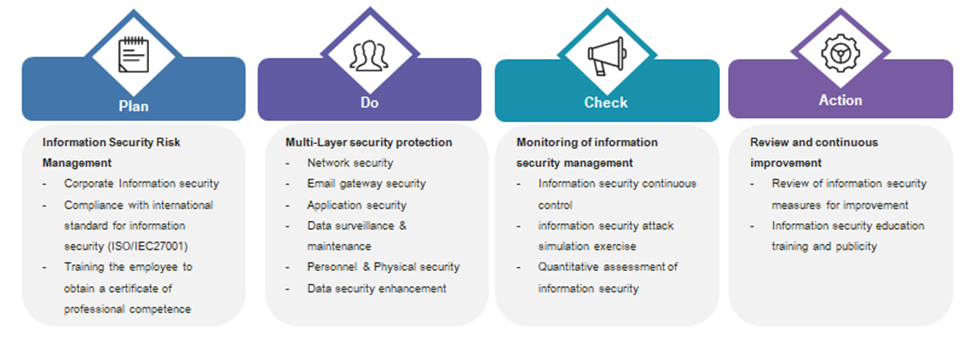
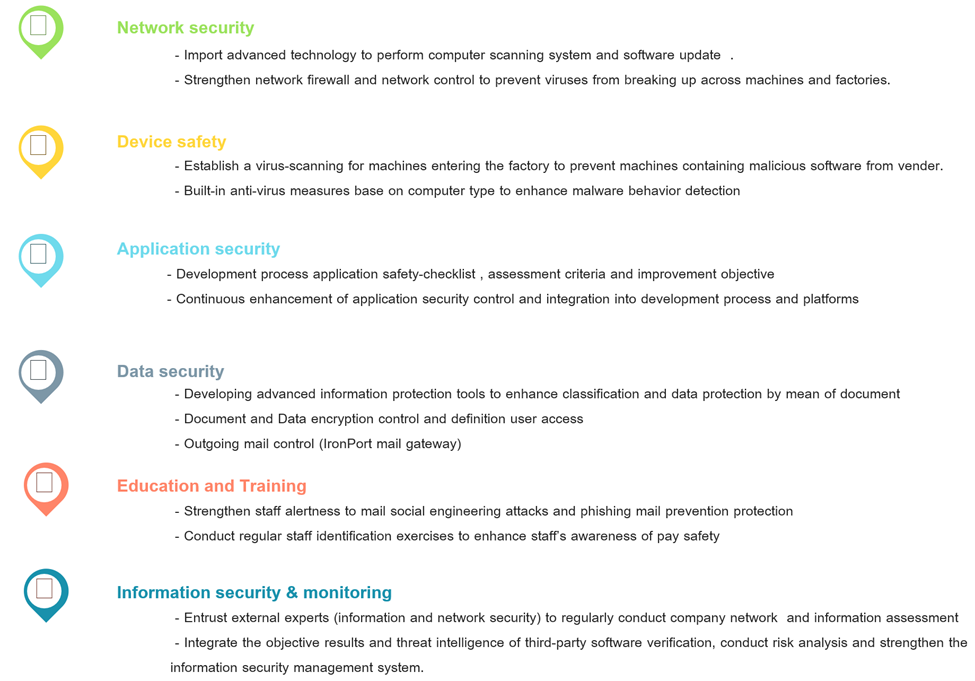
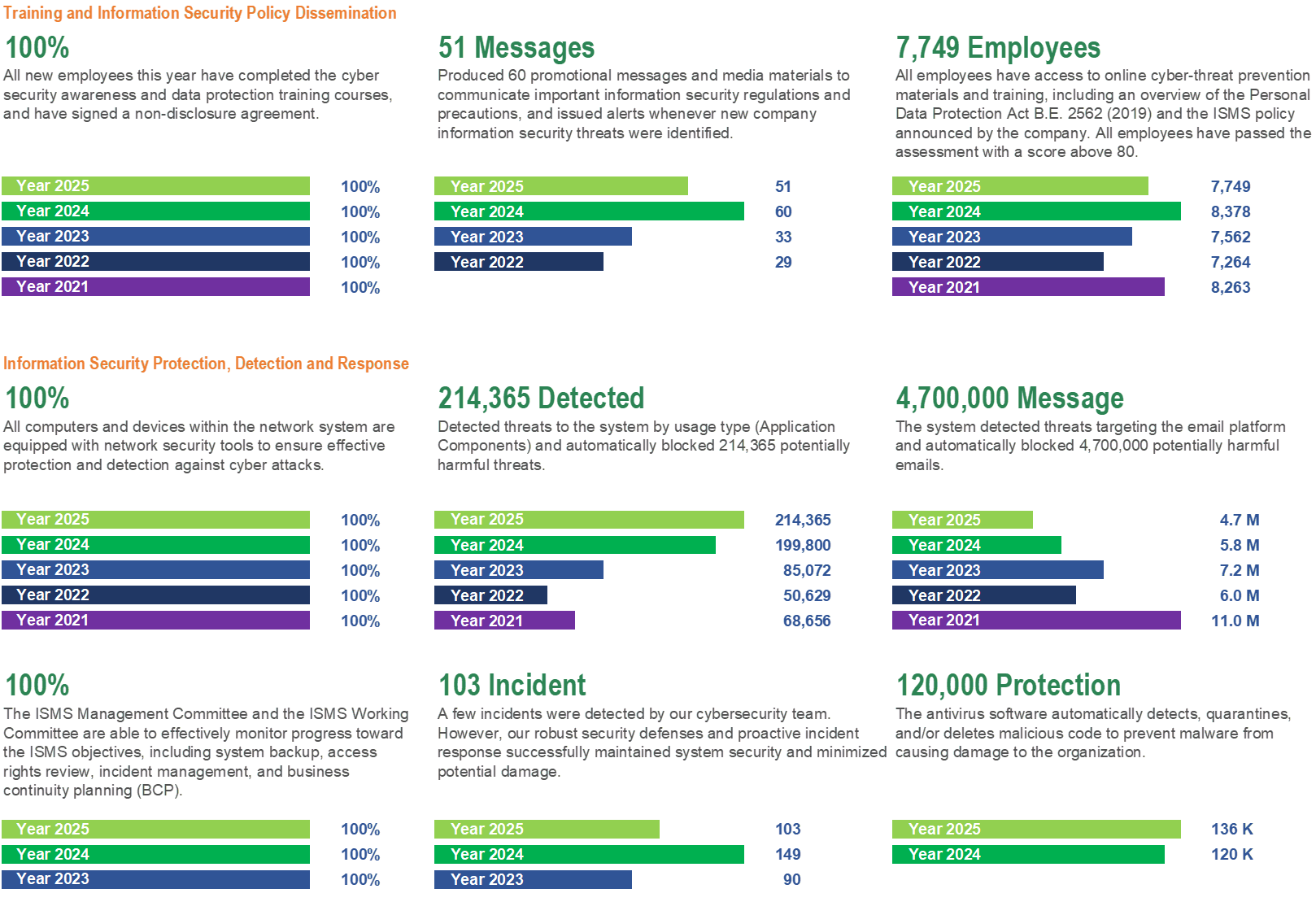
We Respect Your Privacy
Welcome to Apex ! We would like to ensure that you have a safe and pleasant stay on our website. Please accept Cookies for optimal performance, or READ MORE to learn how we use them.
By continuing to use this Website. You agree to our Privacy Policy and our use of Cookies.